Creating or editing a custom security level
PERMISSIONS Security level with Admin permission to configure Resources/Users (HR). Refer to Admin security settings.
NAVIGATION Left Navigation Menu > Admin > Admin Categories > Organization Settings & Users > Resources/Users (HR) > Security > Security Levels
You create a new security level by copying and editing an existing one.
IMPORTANT
• You cannot copy or edit the Dashboard User, Time and Attendance, or Contractor system security levels.
• All other system security levels can be copied, and the copies can be edited.
• It is not possible to deactivate the API User system security level.
How to...
- To open the page, use the path(s) in the Security and navigation section above.
- Right-click an existing security level that best matches the new security level and select Copy Security Level.
IMPORTANT Custom security levels inherit the feature and section access limitations of the security level on which they are based. Make sure you select the closest match. For a description of system security levels that allow you to find the closest match, refer to System security levels.
- Change the name of the security level.
It's a best practice to name your security levels after your job titles. Doing so makes it easy to assign security levels to new hires. - Modify the settings on the General, LiveReports Folders, and Resources tabs. To learn more about each setting, refer to Setting descriptions.
- Click Save, or Save & Close.
Setting descriptions
General tab
Contract permissions define your users' ability to manage contracts. Depending on their level of access, users might be able to set alternate internal costs for labor, modify service/bundle selections, view and generate invoices, access contracts, or manage charges.
To learn how to set user permissions for contract access, review our Contract security settings article.
This section enables you to configure user permissions to access data for organizations and contacts by organization type, configure object permissions for all CRM entities, configure feature access and opportunity checklist and other permissions, and the dashboard for individual organizations. You can designate view, add, or edit permissions on a per-object basis.
To get started with managing your CRM permissions, refer to CRM security settings.
Inventory permissions provide you with the flexibility to define the user groups who can view and manage inventory, and designate the level of inventory management privileges each group has.
For a detailed look at inventory roles and responsibilities, review Inventory security settings.
Autotask enables to you define which user groups can add a new project or view projects. You can also control which groups can see the data contained within projects, reports, and search results. All permissions are by project type. Users with view authorization can also edit and delete where applicable.
To learn more about the permissions you can assign to project users, refer to Project security settings.
In the Service Desk section, you configure View, Add, Edit, and Delete permissions for tickets, ticket notes, and service calls for this security level.
When you're working with Service Desk access permissions, keep the following concepts in mind:
- A Ticket View permission set to All is the default setting for security levels that have access to Service Desk.
- If the Ticket View permission setting is Mine + Organizations, ticket navigation features are displayed, but only tickets and service calls associated with the user will display.
- If the Ticket View permission or Service Call View permission setting is Mine, ticket or service call navigation elements in Autotask, such as links or buttons and the Service Desk option on the Autotask menu, will not be visible.
- On ticket reports and the Ticket page > Related Tickets tab, users without access to a specific ticket will see the ticket number but will be unable to open the tickets or view any other ticket data.
For an in-depth look at Service Desk permissions, review Service Desk security settings.
In the Documents & Knowledge Base section, you configure to grant or restrict access to the knowledge base and document management in Autotask.
This group of permissions provides you with a variety of management tiers that you can assign to your user groups for timesheet administration tasks. You can define access to view, create, and edit timesheets, and enforce required information for the submission of time off requests.
You can learn more about timesheet permissions in our Timesheet security settings article.
Reports permissions empower you to customize the report categories that are accessible to your users. Granting report permissions gives security group members the ability to access the standard pre-built Autotask reports associated with those categories.
TIP LiveReports are published separately; refer to Publishing LiveReports. For more about reports available in Autotask, refer to Reports.
Refer to Report security settings for an in-depth overview of the permissions you can configure for this feature.
Admin settings provide administrator-level access to manage and configure users and features within Autotask. By default, only the security levels System Administrator and Full Access provide comprehensive access to configure Admin features, and the Manager security level provides access to financial features only.
For many Autotask partners, administration workflows can be too complex for a single System Administrator to manage. If your company is facing this challenge, you can delegate the administration of specific areas and feature sets by creating additional security levels with limited access to Admin.
For more information about Admin sections that you can add to any security level, refer to Admin security settings.
You can customize user access levels for Resources/Users (HR), Surveys, Resource Visibility, Client Portal, Form Templates, QuickBooks (New) and miscellaneous other features.
Review Other security settings for information about configuring these resources.
Web Services API permissions give you the ability to control which user groups can access the Autotask Web Services SOAP API and the Autotask REST API. It also defines what actions they can take when interacting with the API.
To learn more, visit our Web Services API security settings article.
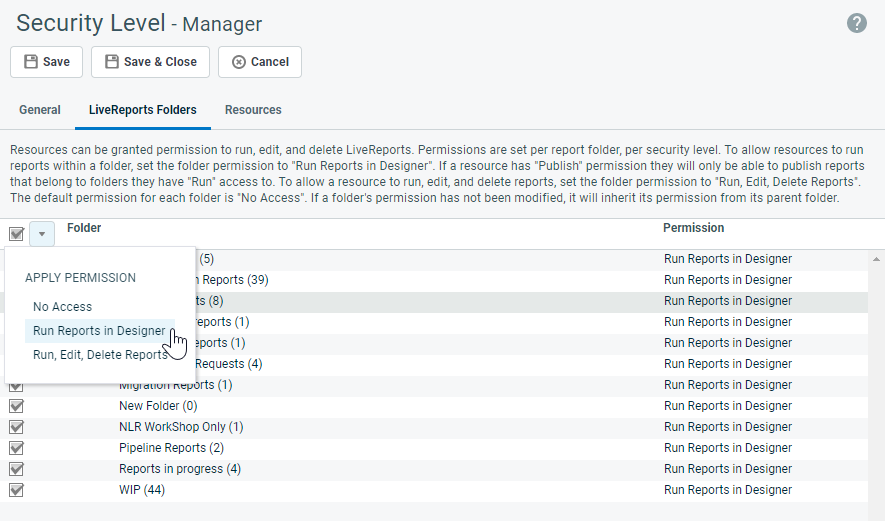
LiveReports Folders Tab
This tab allows Administrators to specify the level of access that each resource with this security level has to each LiveReports folder. Click a row to edit folder permissions. For more information, refer to Configure user access to report folders.
| Permission | Description |
|---|---|
| Folder | This permission displays the folder name as well as a count of reports in each folder (and its sub-folders). To expand the list, click the [+] icon. |
| No Access | If selected, resources with this security level will not see the folder in the list on the LiveReports Designer - Report List view. |
| Run Reports in Designer | If selected, resources with this security level will see the folder in the list on LiveReports Designer - Report List view. They will be able to run reports in this folder but not edit or delete the reports in this folder (unless defined below). |
| Run, Edit, Delete Reports | If selected, resources with this security level will see the folder in the list on LiveReports Designer - Report List view. They will be able to run reports in this folder and edit and delete reports (the Edit and Delete buttons will be visible). |
NOTE If security for an individual folder has not been defined, it will be inherited from its closest parent folder. The default setting is No Access. If a folder's setting is No Access, all of its child folders will automatically be set to No Access.
Resources Tab
Displays a list of all Autotask resources that were assigned this security level, and their current activity status. Editing a resource from this page will open the Resource Management page, where you can assign a different security level. For more information, refer to Adding, editing, or copying a resource.